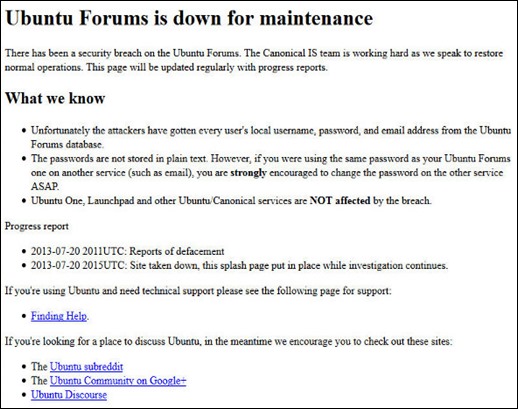
Learn How to Crack IDM manually?
Step 1: First of all Download the IDM trial or If you already have IDM installed Update it by going to Help---}} then to check for Updates.
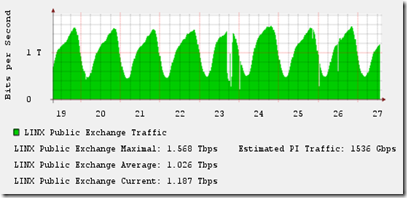
Step 2: Now Go to START => Then go to RUN and type the following text and click enter:
notepad %windir%\system32\drivers\etc\hosts
Step 3: Now right click on hosts file and go to its properties, then go to security tab and then select your admin account, just below you will see an edit button (in front of change permissions), Now give the user full control and write and read rights and then click on apply and then click on Ok, now you will be able to edit the hosts file and save changes in it.
Detail Note about Granting Permission In Windows 7:
For Windows 7 users, due to security reasons you will not be able to save hosts file.so follow this steps :
First of all go to C:/ drive then go to Windows Folder and then go to System32 folder and then go to Drivers folder and then go to Etc Folder, in the Etc folder you will see the hosts file.
Now right click on hosts file and go to its properties then go to Security tab select Users under Group or user names and click on edit button,Permission For Host Window will get open, in that window select Users account and grant permission in bellow section which is "Permission for SYSTEM" by clicking all checkbox under "Allow" Name and press Ok. Dont click on any Deny check box.
Note : If you have login through admin then skip this step6 .Its just for granting permission for editing file.
Step 4: Thus a notepad file appears something like this as shown below:

Now copy the below lines of code and add to hosts file as shown above image box :
127.0.0.1 tonec.com
127.0.0.1 www.tonec.com
127.0.0.1 registeridm.com
127.0.0.1 www.registeridm.com
127.0.0.1 secure.registeridm.com
127.0.0.1 internetdownloadmanager.com
127.0.0.1 www.internetdownloadmanager.com
127.0.0.1 secure.internetdownloadmanager.com
127.0.0.1 mirror.internetdownloadmanager.com
127.0.0.1 mirror2.internetdownloadmanager.com
After adding these piece of code, save the notepad file. And exit from there. Step 5: Now open IDM and click on Registration. When you click on registration, Now a new dialog(window) appears that is asking for Name, Last Name, Email Address and Serial Key.
Step 6: Hence Enter you name, last name, email address and in field of Serial Key enter any of the following Keys:
RLDGN-OV9WU-5W589-6VZH1
HUDWE-UO689-6D27B-YM28M
UK3DV-E0MNW-MLQYX-GENA1
398ND-QNAGY-CMMZU-ZPI39
GZLJY-X50S3-0S20D-NFRF9
W3J5U-8U66N-D0B9M-54SLM
EC0Q6-QN7UH-5S3JB-YZMEK
UVQW0-X54FE-QW35Q-SNZF5
FJJTJ-J0FLF-QCVBK-A287M
And click on ok to register.
Step 7: After you click ok, it will show an message that you have registered IDM successfully.
Now start your Internet download manager, and now you IDM has been converted to full version and specially when you update next time, your registration will not expire.
That means it will remain full version for life time and you can update it without any problem in future. That’s it!
Your Job gets done and any comments are welcomed below for this article. Enjoy…





















 PayPal
PayPal