How to Clean your Mac System Comprehensively







We call it the internet and its defining feature has always been the connection that people can form over very vast distances. It was only natural that we would figure out a way to use the new technology to share data and media in real time. Today this is called Peer-to-Peer sharing and everything from virtual currencies to music videos is shared in this way.
P2P file sharing or torrenting has brought down the barriers to data and information that existed before. But there are still a few places where the internet is restricted.
If you find that you live in a country where the government monitors and censors the internet, it may be time to get yourself a VPN to circumvent such restrictions and unlock the full potential of the internet.
Assuming you’ve already read up about VPNs, here is our list of the top 5 best VPNs designed for file sharing and torrenting.
This one is more of an extension on chrome, but it works extremely well and that’s why it’s on the list. The company behind this extension started off by making a VPN dependent on the operating system. They established themselves as a serious player based on their high quality service and overall dependability.
Now, with a Chrome app that has 256-bit AES encryption, they’ve upped the game while maintaining the same level of service. If you use Chrome and download torrents, this is the one you should get. Get CyberGhost.
Good Speed? Good Connectivity? Great Encryption? All yes with Private Internet Access. This provider offers a 256-bit AES OpenVPN encryption which is state-of-the-art.
There is also an option to pay with Bitcoin, They’ve got special apps that let you kill individual apps and save data from leaking out of the system.
What’s the issue? Their servers are based in the United States. Considering the technical capabilities of the US Government and the local laws concerning copyright infringement and file sharing, this may be an issue for most.
Then there is the issue that the Android app is much better designed than the iOS app. People who work with the company complain about slow and laggy software on both OSX and iOS.
That’s the only reason this one features on our list, otherwise it’s perfectly fine. Try it out.
Extremely secure software by a company based in the US. They run their operations in 23 countries, however, and are open to the idea of moving if the legal regulations here get too tight.
Bittorrent is only allowed on certain servers and in select locations but when you do get access to it the service works extremely well. The reason they don’t let people torrent from all servers at once is because of the intense usage torrenting and file sharing involves. But the service is secure and performs well overall.
Regardless of where you are trying to share files from, the servers will automatically route to one of the locations where the system is optimized for heavy-duty use. This makes TorGuard one of the best options for torrents and file-sharing online.
If you’ve never heard of VPNArea, that could be because it is a startup based in Bulgaria. Despite being a young company, the team have developed some pretty interesting features.
They offer an auto IP changing feature, a per-app kill switch and a DNS leak protector. If you sign up with them you can bet you will be using these handy tools often.
The issue with VPNArea is that the software could have been much better. The security features aren’t up to the mark (they use a 128-bit Blowfish encryption) and there are minor issues with the design of the software itself.
But considering they are new and offer a 7-day free trial, you may want to check them out anyway.
BolehVPN is based in Malaysia and is used by a surprising number of people in and around Asia. It’s got good speed and low prices going for it after all.
Plus the software is optimized for use with BitTorrent.
But the website and software are very badly designed and often confusing to use. The cluttered website and the sub-par encryption could be the reason why this one features on the bottom of our list.
There are a lot of countries with restricted access to information and the internet in general. Certain useful media and documents are completely off limits for people who live in these places.
By using an effective VPN, you can cover your data and protect your network from any snooping. You’ll want to find a balance between the right price, great security and flawless connections. With enough time and research you may be able to find the best one for you.
This was contributed by Caroline, a technology enthusiast whose main area of interest is internet security. Caroline recommends www.securethoughts.com as of the best possible online sources for information regarding internet security.



inurl:index.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurllay_old.php?id=
inurl:declaration_more.php?decl_id=
inurlageid=
inurl:games.php?id=
inurlage.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=d=
inurl:event.php?id=
inurlroduct-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:fiche_spectacle.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurltray-Questions-View.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?av
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurlreview.php?id=
inurl:loadpsb.php?id=
inurlpinions.php?id=
inurl:spr.php?id=
inurlages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurlarticipant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurlrod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurlerson.php?id=
inurlroductinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurlrofile_view.php?id=
inurl:category.php?id=
inurlublications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurlrod_info.php?id=
inurl:shop.php?do=part&id=
inurlroductinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurlroduct.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurlroduit.php?id=
inurlop.php?id=
inurl:shopping.php?id=
inurlroductdetail.php?id=
inurlost.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurlage.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurlroduct_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:tran******.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurlroduct-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:review.php?id=
inurl:loadpsb.php?id=
inurl:ages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurlpinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurlffer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
inur l: info.php?id=
inurl : pro.php?id=
inurl:index.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurllay_old.php?id=
inurl:declaration_more.php?decl_id=
inurlageid=
inurl:games.php?id=
inurlage.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurltray-Questions-View.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?avd=
inurl:event.php?id=
inurlroduct-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:fiche_spectacle.php?id=
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurlreview.php?id=
inurl:loadpsb.php?id=
inurlpinions.php?id=
inurl:spr.php?id=
inurlages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurlarticipant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurlrod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurlerson.php?id=
inurlroductinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurlrofile_view.php?id=
inurl:category.php?id=
inurlublications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurlrod_info.php?id=
inurl:shop.php?do=part&id=
inurlroductinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurlroduct.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurlroduit.php?id=
inurlop.php?id=
inurl:shopping.php?id=
inurlroductdetail.php?id=
inurlost.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurlage.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurlroduct_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:tran******.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurlroduct-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:review.php?id=
inurl:loadpsb.php?id=
inurl:ages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurlpinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurlffer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
inurl:shop+php?id+site:fr
"inurl:admin.asp"
"inurl:login/admin.asp"
"inurl:admin/login.asp"
"inurl:adminlogin.asp"
"inurl:adminhome.asp"
"inurl:admin_login.asp"
"inurl:administratorlogin.asp"
"inurl:login/administrator.asp"
"inurl:administrator_login.asp"
inurl:"id=" & intext:"Warning: mysql_fetch_assoc()
inurl:"id=" & intext:"Warning: mysql_fetch_array()
inurl:"id=" & intext:"Warning: mysql_num_rows()
inurl:"id=" & intext:"Warning: session_start()
inurl:"id=" & intext:"Warning: getimagesize()
inurl:"id=" & intext:"Warning: is_writable()
inurl:"id=" & intext:"Warning: getimagesize()
inurl:"id=" & intext:"Warning: Unknown()
inurl:"id=" & intext:"Warning: session_start()
inurl:"id=" & intext:"Warning: mysql_result()
inurl:"id=" & intext:"Warning: pg_exec()
inurl:"id=" & intext:"Warning: mysql_result()
inurl:"id=" & intext:"Warning: mysql_num_rows()
inurl:"id=" & intext:"Warning: mysql_query()
inurl:"id=" & intext:"Warning: array_merge()
inurl:"id=" & intext:"Warning: preg_match()
inurl:"id=" & intext:"Warning: ilesize()
inurl:"id=" & intext:"Warning: filesize()
inurl:"id=" & intext:"Warning: require()
inurl:index.php?id=
inurl:trainers.php?id=
inurl:login.asp
index of:/admin/login.asp
inurl:buy.php?category=
inurl:article.php?ID=
inurl:play_old.php?id=
inurl:declaration_more.php?decl_id=
inurl:pageid=
inurl:games.php?id=
inurl:page.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurl:Stray-Questions-View.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?avd=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:ogl_inet.php?ogl_id=
inurl:fiche_spectacle.php?id=
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:opinions.php?id=
inurl:spr.php?id=
inurl:pages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurl:participant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:prod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurl:person.php?id=
inurl:productinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurl:profile_view.php?id=
inurl:category.php?id=
inurl:publications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurl:prod_info.php?id=
inurl:shop.php?do=part&id=
inurl:productinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurl:product.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurl:produit.php?id=
inurl:produit.php?id=+site:fr
inurl:pop.php?id=
inurl:shopping.php?id=
inurl:productdetail.php?id=
inurl:post.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurl:page.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurl:product_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:transcript.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:pages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurl:opinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurl:offer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
inurl:index.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurllay_old.php?id=
inurl:declaration_more.php?decl_id=
inurlageid=
inurl:games.php?id=
inurlage.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurltray-Questions-View.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?avd=
inurl:event.php?id=
inurlroduct-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:fiche_spectacle.php?id=
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurlreview.php?id=
inurl:loadpsb.php?id=
inurlpinions.php?id=
inurl:spr.php?id=
inurlages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurlarticipant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurlrod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurlerson.php?id=
inurlroductinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurlrofile_view.php?id=
inurl:category.php?id=
inurlublications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurlrod_info.php?id=
inurl:shop.php?do=part&id=
inurlroductinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurlroduct.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurlroduit.php?id=
inurlop.php?id=
inurl:shopping.php?id=
inurlroductdetail.php?id=
inurlost.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurlage.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurlroduct_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:transcript.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurlroduct-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:review.php?id=
inurl:loadpsb.php?id=
inurl:ages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurlpinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurlffer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
That’s it, ALL DONE. I hope these Google Dorks will really help you in hacking a webpage using SQL Methods. Please use this article as informative basis. If you have any doubt left, then let me know in the Comments below and must share this article as well. Till then Google Night and Have fun.
Also SEE- PayPal Hacking - Bypass PayPal payment to get Free Products Online


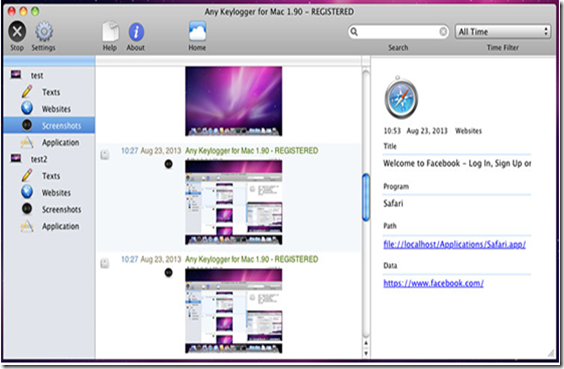
This is known as The world's best keylogger software for Mac. With 6 basic but effective features Any Keylogger for Mac can help users record almost all activities happened on Mac in stealthy mode. Therefore Anykeylogger for Mac is a simple and user-friendly keylogger app, which can record Mac activities such as browsed sites, keystrokes and screenshots.
Now With simple interface and effective monitoring features, Any Keylogger for Mac has won a number of Mac users and awards. Any Keylogger for Mac is a good solution to Mac activity monitoring and many more.
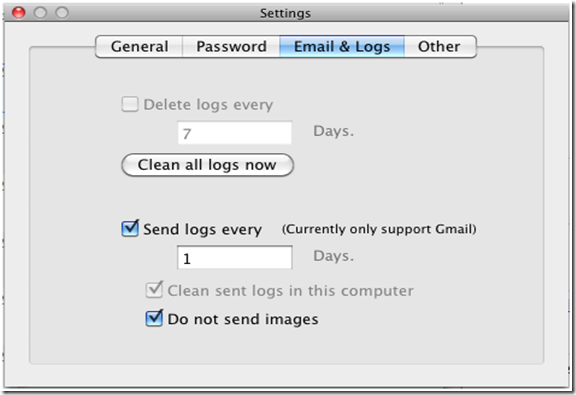
Well Any Keylogger for Mac secretly works in the background process and cannot be detected by users as well as antivirus software too. It can record all activities on your Mac PC including texts typed, website visited, screenshots, send logs via email and applications launched etc. Thus It will automatically operate in 100% hidden mode when you boot up your Mac.
1. Take Screenshots
2. Record Browsed Sites History
3. Log Keystrokes
4. Record Program Activity
5. Send The Logs Via Email
6. Run in stealth Mode
1. First of download and install the AnyKeylogger for Mac in your Operating System.
2. Now You will be prompted to install a monitoring tool. When you install the program, it will automatically run when your computer starts always.
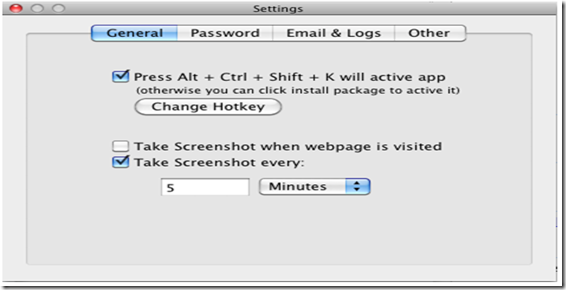
3. Then Click on “Settings” in the main interface, choose “Common”, setup time intervals of screenshots, screenshots of visited web pages or activated windows. When done, you can close the settings window. Or you can define Hotkey combination to view logs here.
I hope you all liked my article on Keylogger for MAC OX, thus If you want to track children’s online activities to check whether they have browsed inappropriate sites. Or you just need a keylogger to record what you yourself have done on Mac, this is best for you. So what are you waiting for, just download the keylogger now and Have fun. If you have any doubts left in your mind, then let us know in the comments. Till then Good Bye.

Do you Want to Access Facebook on Blocked Network?

Also SEE- How To Access Blocked Social Networking Sites?
How to Open Blocked Torrent Sites in India
Facebook Proxy Sites are those which would help you to access or login Facebook at Blocked Network’s. Many times when you are trying to use Internet at the public Wi-Fi network or your office network, then you are not able to get through it. This is all because of admin of the public network places due to security reasons. But if you have the access to Facebook Proxy Login websites, then you can easily get through these blocked sites without any doubt.
Facebook Proxy is a especially dedicated for the aim of unblocking Facebook. This website allows you open Facebook from anywhere. While you are at office, school or any other organization this site will help you to access you Facebook account in a very simple manner. Just on the Home screen enter the Facebook URL and click "Go" , hence It will open the Facebook homepage for you.
Proxymice is a Facebook proxy site created by a group of professional web developers specially for those who wish to cant access Facebook normally. As compared to other fast browsing sites list, Give it a try and you wont be regret. They have provided a link in their sidebar that reads "Start Facebook Proxy" so that users can directly move to Facebook etc. Its so simple to use this.
With the help of this proxy websites you will be able to break through all the network barriers to get access to your FB account such as Cyberoam. With the help of this site, not only can you get into your Facebook (FB) account, but can also browse through other sites as well. Now You have to go to the website and enter the URL to get the page where you can enter the credentials to access your account. That’ it!
All Done! I hope now it would be easier to access Facebook without any problem at blocked network. In case if you face any difficulties while using these Facebook login proxies, let us know. Now If you found this article useful, then please share this with all your friends or colleagues online/offline. Till then Peace!
Must SEE- Top 20 Methods on How to Hack Facebook Password in 2013




The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.
Bug is in the OpenSSL's implementation of the TLS/DTLS (transport layer security protocols) heartbeat extension (RFC6520). When it is exploited it leads to the leak of memory contents from the server to the client and from the client to the server.
1.) First of all check if the sites you use every day on an individual basis are vulnerable to Heartbleed bug or not using http://filippo.io/Heartbleed/, and if you're given a red flag, avoid the site for now.
2.) LastPass also created a Web app that will tell you what kind of encryption a site uses, and when the encryption was last updated.
3.) Provensec also created a scanner at http://provensec.com/heartbleed/
4.) GlobalSign SSL Configuration Checker.
That’s it! Enjoy and Be Safe. Any Comments are welcomed below.

If our Tutorials have helped you a little, then kindly spread our voice using the button below:-

| KrackoWorld (KoW) © 2014. All Rights Reserved | Style By All Web Designing | About | Contact |