How to find a Vulnerable Website and Start Hacking?
|
|
Now a days Website Hacking has become a tradition or fun to create problems for other people. Hackers are searching for finding the holes in the websites having high page ranks and traffic. Who knows what the hackers are going to do or their next target is on your site? Few years back there is not so much terror of being website hacked because at that time there is not so much of powerful tools developed by humans, but now the time is that even a newbie can find a vulnerable website and start hacking.
Audit your website security with Acunetix Web Security Scanner
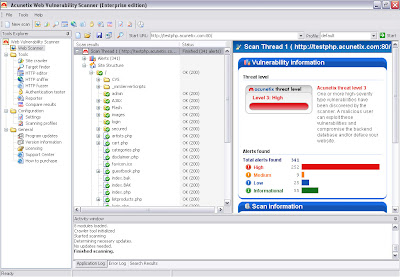
Website security is possibly today's most overlooked aspect of securing the enterprise and should be a priority in any organization. Hackers are concentrating their efforts on web-based applications - shopping carts, forms, login pages, dynamic content, etc. Web applications are accessible 24 hours a day, 7 days a week and control valuable data since they often have direct access to backend data such as customer databases.
Firewalls, SSL and locked-down servers are futile against web application hacking
Any defense at network security level will provide no protection against web application attacks since they are launched on port 80 - which has to remain open. In addition, web applications are often tailor-made therefore tested less than off-the-shelf software and are more likely to have undiscovered vulnerabilities. Acunetix WVS automatically checks your web applications for SQL Injection, XSS & other web vulnerabilities.
Commonly used Tool to find a vulnerable website
Acunetix-
Acunetix is the world’s best tool developed to find a venerability in any web application as It automatically checks your web applications for SQL Injection, XSS & other web vulnerabilities.
Acunetix Web Vulnerability Scanner includes many innovative features:
- An automatic client script analyzer allowing for security testing of Ajax and Web 2.0 applications
- Industries' most advanced and in-depth SQL injection and Cross site scripting testing
- Advanced penetration testing tools, such as the HTTP Editor and the HTTP Fuzzer
- Visual macro recorder makes testing web forms and password protected areas easy
- Support for pages with CAPTHCA, single sign-on and Two Factor authentication mechanisms
- Extensive reporting facilities including VISA PCI compliance reports
- Multi-threaded and lightning fast scanner crawls hundreds of thousands of pages with ease
- Intelligent crawler detects web server type and application language
- Acunetix crawls and analyzes websites including flash content, SOAP and AJAX
- Port scans a web server and runs security checks against network services running on the server
Download Acunetix Web Security Scanner
Enjoy!
Join me on Google+
|
|
Respected Readers :-
|

E njoyed this post very much – So why not you Subscribe to our regular Email Updates ! and stay connected with us forever .



















hey karan from which site you get this text banner image which is on top.
ReplyDeleteabhishek
@ abhishek
ReplyDeleteI dont get your answer,please explain me in more details.
karan open this image http://2.bp.blogspot.com/-8YCb-ymj7Qg/Tc4VVfkkGgI/AAAAAAAAAts/KukB6uaIpls/s1600/Logo%2BTemplate%2B-%2Ba_Logo_12.jpg how did you make this? i found it very cool image for blog please tell me how you have made it can you made one for me? i'll be very thankful to you.
ReplyDelete@ Anonymous
ReplyDeleteI will make this image form adobe Photoshop.
but from where you've got the background please give me the link.you know karan a blogger blog because he want's to share the things that he know so please help me.
ReplyDelete@ Anonymous
ReplyDeleteThese banners,logos,posters and images are copyright protected under me,you cannot use them for different purposes.
Moreover, any other help is welcomed.
ok, then karan tell me how you've make Your Help Is Precious?
ReplyDelete@ Anonymous
ReplyDeleteMy site is all about ethical hacking and security tips not about blogging resources,widgets,css,htmls,if you want to know problems regarding your template and widgets then please visit www.mybloggertricks.com, www.allblogtools.com etc.
Any help regarding ethical hacking and so on is purely welcomed.
http://www.reclamando.com.br/?system=news&action=read&id=14376%27
ReplyDeletevulnerable site
Do you need the service of an hacker pretty bad? Redhacker is the real and legit hacker out there. I hired his service for my whatsapp hack,Gmail hack,bank account hack and he delivered perfectly. He can be trusted. Contact: redhackar8920@gmail.com
ReplyDeleteThe extensively held belief is that the kings and also queens Dog Harness Reviews of classical times were the very here first to style and use dog collars.
ReplyDelete