Spyware Cease Features
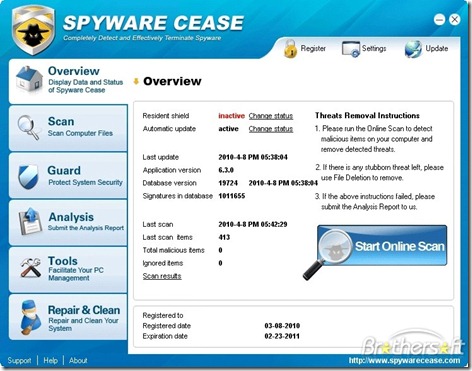 1.Internet Tracks and Password Thieves Cleaner
1.Internet Tracks and Password Thieves Cleaner
One simple click to delete malicious cookies from your computer system so as to clear Internet Tracks completely and minimize password thieves to protect your privacy!
2.Real-Time Guard (NEW)
Spyware Cease™ offers the real-time guard function to protect your PC from potential threats, minimizing interruptions. Spyware Cease will inform you by displaying a popup on the bottom right of the screen, whenever any program attempts to modify registry, so that your PC is always protected against spyware threats.
3.Deep Scan
Spyware Cease™ will completely scan your system registry and hard drives for spyware programs that installed on your PC. The free full scan will identify and list all threats.
4.Powerfully Remove Spyware
After scanning, Spyware Cease™ will clean up all malicious spyware programs that can continually generate unwanted popups, slow down PC speed, and hijack homepage, etc. The spyware programs include but are not limited to:
- Adware
- Annoyance
- Browser Helper Object
- Cracking Tool
- Dialer
- Downloader
- Encryption Tool
- Exploit
- Rogue Security Software
- FTP Server
- Hijacker
- Hostile ActiveX
- Key Logger
- Nuker
- Password Cracker
- Phreaking Tool
- Proxy
- SPAM Tool
- Tracking Cookie
- Trojan
- Worm Creation Tool
- Usage Tracks
- P2P
- Mail Bomber
- Phreaking Tool
5.Auto & Scheduled Scan
By default, Spyware Cease™ will run a quick scan to the System Processes, Windows Directory and Users Directory for spyware programs. This is the most reliable way to clean up threats on your PC and restore your Internet confidence . Automatic scan can be scheduled by setting Schedule Task and Start time for the program to meet your need.
6.System Analysis (NEW)
By diagnosing PC System drivers, System process, HOSTS files, System services and Windows registry, Spyware Cease™ will generate a text that shows all Windows system information.
You can receive a customized solution for your specific problem on your individual system, once you forward the Analysis Report and Scan Results LSR.lsr to Spyware Cease support team.
7.Ignore Items
After a scan is performed, you can right-click on the detected result to add the item to the Ignore List so that Spyware Cease™ will not remove the item and will ignore it on the next scan.
8.Auto and Manual Update
By default, Spyware Cease™ will automatically check for update as it starts up, or you can manually check for updates in the "Update" section.
9.Vulnerability Scanner and Patch (New)
Spyware Cease™ offers a suite of solutions to determine the configuration of every system service, and then compares the data found to thousands of vulnerabilities in its existing database.
If any potential vulnerability is identified, Spyware Cease™ will repair it with the latest patch to greatly enhance the security of your computer system.
10.Editors rating - 9/10 and McAfee SECURE.
![download_buttons1[2] download_buttons1[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiQ_6iFUCU-jxRFsRkFHyG6D40weqJ7d5R-b8OSCAa4KrTAegMRk6bGzoMPd6Y7aMXBQHN9pInENvy5h6WLup9MMtV9YfTEt38G5t5QM8NSSe2HSNUox75zcXxZAPDeMQnIpLgwO8XpnPFO//?imgmax=800)












![download_buttons1[2] download_buttons1[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiQ_6iFUCU-jxRFsRkFHyG6D40weqJ7d5R-b8OSCAa4KrTAegMRk6bGzoMPd6Y7aMXBQHN9pInENvy5h6WLup9MMtV9YfTEt38G5t5QM8NSSe2HSNUox75zcXxZAPDeMQnIpLgwO8XpnPFO//?imgmax=800)