Latest AnyKeylogger for Mac 2014: Free Download

What is Any Keylogger for Mac?
This is known as The world's best keylogger software for Mac. With 6 basic but effective features Any Keylogger for Mac can help users record almost all activities happened on Mac in stealthy mode. Therefore Anykeylogger for Mac is a simple and user-friendly keylogger app, which can record Mac activities such as browsed sites, keystrokes and screenshots.
Now With simple interface and effective monitoring features, Any Keylogger for Mac has won a number of Mac users and awards. Any Keylogger for Mac is a good solution to Mac activity monitoring and many more.
How it Works?
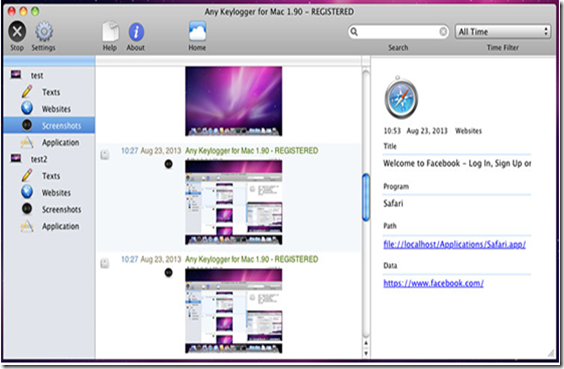
Well Any Keylogger for Mac secretly works in the background process and cannot be detected by users as well as antivirus software too. It can record all activities on your Mac PC including texts typed, website visited, screenshots, send logs via email and applications launched etc. Thus It will automatically operate in 100% hidden mode when you boot up your Mac.
AnyKeylogger Features:
1. Take Screenshots
2. Record Browsed Sites History
3. Log Keystrokes
4. Record Program Activity
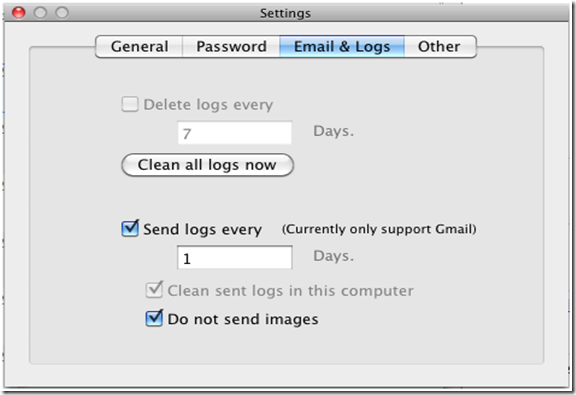
5. Send The Logs Via Email
6. Run in stealth Mode
How to Install and Use Anykeylogger to record Mac activities?
1. First of download and install the AnyKeylogger for Mac in your Operating System.
2. Now You will be prompted to install a monitoring tool. When you install the program, it will automatically run when your computer starts always.
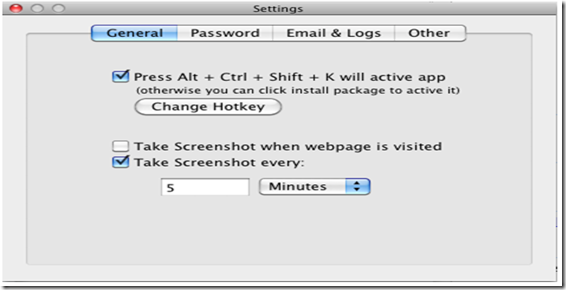
3. Then Click on “Settings” in the main interface, choose “Common”, setup time intervals of screenshots, screenshots of visited web pages or activated windows. When done, you can close the settings window. Or you can define Hotkey combination to view logs here.
Final Words:
I hope you all liked my article on Keylogger for MAC OX, thus If you want to track children’s online activities to check whether they have browsed inappropriate sites. Or you just need a keylogger to record what you yourself have done on Mac, this is best for you. So what are you waiting for, just download the keylogger now and Have fun. If you have any doubts left in your mind, then let us know in the comments. Till then Good Bye.























