Get 3G Speed in 2G plans - Nokia Switching Network Techniques In All Operators
Wow! Its KrackoWorld official technique of hacking 3G in 2G plans for all operators like Aircel,Tata DoCoMo,Airtel,Reliance,Bsnl and Vodafone. Last night I am surfing 2G in my Nokia C6 phone and suddenly switched my network to UMTS and you will be shocked to know I am getting 3G signals along with 3G speed(around 75% of 3G speeds). Then I tried this scheme in all operators and worked 100% successfully. This trick or we can say hack is working best with Aircel.
Procedure of this trick
Note- This trick is for Nokia Mobiles only because they support Switching the gears(Network) technique.
1. First connect your phone with Nokia pc suite or ovi software in GSM mode(2G mode).
2. After your Nokia modem gets connected successfully to the internet, adopt this trick given below-
Go to menu-settings-phone-network and change GSM to UMTS.
3. Done! you have hacked 3G and always make sure to change to GSM after disconnecting your phone to PC etc..
PS: Please make sure while you connect next time your phone to PC, the phone must be in 2G mode and after get connected, switch to 3G otherwise your balance will be deducted according to 3G plans.
Enjoy na! Please pass your comments…




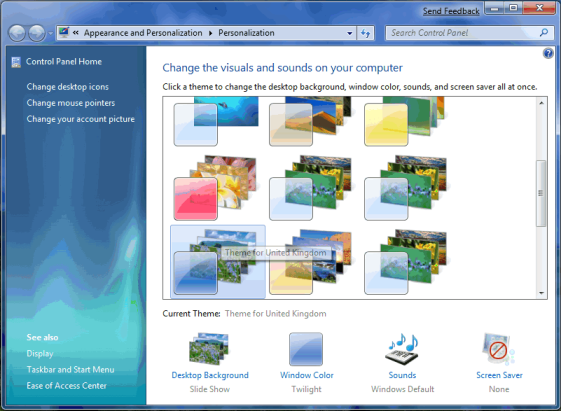 As you all know Windows 7 is a 64-bit windows with superior graphics and high resolution.Surfing wallpapers,games and themes on it makes a lot of fun.Windows 7 has been a real delight for the eyes due to its excellent graphics.Therefore,today we will unblock its some of the hidden themes using a simple trick or code.By default Windows 7 has 5 themes enabled for all countries but there are additional themes which are country specific and enabled according to your demographic location.Here i will show you how to enable/unlock the country specific hidden themes in windows 7.Once enabled these themes will always be available to you.The best method is explained here on our Site.It enable these hidden themes…
As you all know Windows 7 is a 64-bit windows with superior graphics and high resolution.Surfing wallpapers,games and themes on it makes a lot of fun.Windows 7 has been a real delight for the eyes due to its excellent graphics.Therefore,today we will unblock its some of the hidden themes using a simple trick or code.By default Windows 7 has 5 themes enabled for all countries but there are additional themes which are country specific and enabled according to your demographic location.Here i will show you how to enable/unlock the country specific hidden themes in windows 7.Once enabled these themes will always be available to you.The best method is explained here on our Site.It enable these hidden themes… 















