31 March 2012
27 March 2012
How To Access Blocked Social Networking Sites?
Labels - Cookie and Session Hijacking , IP Address , Website Hacks
Using IP Instead Of URL
- This depends on the software/application used. Sometimes blocked sites are stored as a list of URLs (eg. www.yahoo.com, www.donwload.com,etc) and typing the IP instead of the URL might sometimes work. In a local computer, doing a ping domain.com command in Command Prompt (Mac users use Terminal) will return you the IP address. You can also do it online via www.whatsmyip.org
23 March 2012
How To See Deleted Or Unavailable Pictures On Facebook
Labels - Hack facebook , News , Website Hacks
22 March 2012
Airtel Prepaid 10 Paise Per Minute Call
15 March 2012
Recharge Mobile Using ATM Card
Many time to recharge your cell phone,dth,data card and other useful service you have to go nearest recharge shop and sometimes you have to wait a long time for recharge which is very embarrassing.So today I am going to post a online recharge website which is fully secured and you can enjoy to recharge online without wasting your time.
How to Find Fake Email Address?
![]() Hello Friends,Daily we got almost 100's of fake emails,Like in Spam folder.A php script can mail you from any email address.Also from your own email address.Strange ?But its true.So today I am going to post a very informative article on How To Find Fake Email Address.With time to time people creates many fake email id's, for its fun,hacking and other purpose,which creates a bunch of troubles to thousand of peoples.So detection of fake email id's is very important because hackers are always looking to use the Fake Email ID'S to get personal information of a victims.There are several techniques to identify fake email id's.
Hello Friends,Daily we got almost 100's of fake emails,Like in Spam folder.A php script can mail you from any email address.Also from your own email address.Strange ?But its true.So today I am going to post a very informative article on How To Find Fake Email Address.With time to time people creates many fake email id's, for its fun,hacking and other purpose,which creates a bunch of troubles to thousand of peoples.So detection of fake email id's is very important because hackers are always looking to use the Fake Email ID'S to get personal information of a victims.There are several techniques to identify fake email id's.
Email Address Checker:-
Email Address Checker is well known email IDs checker which identify the the validity of any kind of emails IDs. All you need to do is type the email IDs in the box and press ‘Check’ button. Within a moment it displays the validity of email IDs.
Visit : Click Here
Put the email Id you want to scan in check box and click on check for processing:-
Click on info button to find the email is true or false
Click on Result and see the result that is email is valid or not
Voillaaa !!! Email is valid and also in good use.This is the demo that how you can find fake emails.Copy the email id in your scam box and put it in scanner box and find the result
About The Author
This article has been written by-Sunil ThakurVisit Our Site-www.hackingworld.in
Join him on Facebook-facebook.com/lovi.76
10 March 2012
Facebook Hacked! Victim of DDOS Attack
Labels - Hack facebook , News , Website Hacks

What happens to Facebook in Europe recently?
Recently at 18:00 AM 8/03/2012 , Facebook falls under this attack in most of the countries like Europe, France, Germany, Russia and South Africa where its servers becomes irresponsible and service gets temporarily down for some time (approximate for 2 hours). Third parties suggested a problem with Facebook's European DNS servers may have been at the root. These machines connect the address "Facebook.com" with the actual content of the website, and during the outage attempts to contact to them as normal received no response.
DownRightNow, which monitors major web services, showed Facebook having suffered ongoing intermittent service until mid-afternoon.CERT. Be, a Belgian government agency, claimed that the outage was due to a DDOS hacker attack, but this has not been confirmed.
Latest Facebook Security Update-
The issue has been now fully resolved and everyone should have access to Facebook. We apologies for any inconvenience occurred.
That’s it!
09 March 2012
John the Ripper- Intro and How to Use?
Labels - Download Softwares , How to , Others , Password Cracking

Types of Attacks-
John the Ripper can perform mainly 2 types of attacks mentioned below-
1. Dictionary attacks
2. Brute Force mode
Download-
Now its available for Windows, Linux, Mac OS X types of operating system. To download it, please refer to its official website at here.
That’s it! All the best…
08 March 2012
Hacking Facebook Fan Pages through Exploit

What we need to hack Facebook Fan Page:
1. An exploit
2. Free web hosting site
3. Key to run the exploit
4. Your Facebook Email id
Procedure for hacking Facebook Fan page:
1. First of all download Facebook hacking exploit from here.
2. After downloading, open and extract all the files inside(2 files).
3. Now open pagehack.js and some some necessary changes as given below-
Search for Facebook-email-id@gmail.com and replace it with your Facebook email id.
4. Now Upload the first pagehack.js file to any free webhosting site like my3gb.com, 000webhost.com etc.
5. After uploading, check the root of your pagehack.js file and copy it.
6. Now its time to make changes in your second key for pagehack.txt file as given below-
Open and replace www.yourhostingwbesite.com/pagehack.js with your pagehack.js root in your free webhosting site to link both files properly to each other.
7. After making changes to key for pagehack.txt, simply upload it to same webhosting site along with paghack.js file.
8. Now copy the JavaScript as mentioned in the Key for pagehack.txt file and send it to your victims and ask him to paste in your browser and see the magic or something else.
9. Immediately after your victims do it, he/she will be successfully hacked.
10. That’s it! You have hacked Facebook fan page by yourself. Enjoy!!!
Note- KrackoWorld is not responsible for any kind of damage you done by this script as this is made for the educational purposes only.
07 March 2012
Latest Tata DoCoMo 3G/3.5G HSDPA Hack 2012

Procedure for Tata DoCoMo 3.5G hack (High speed downloading)
1. First of all activate an 3G plan in DoCoMo worth Rs 11.
2. Now immediately activate any 2G plan of Rs 15, 69 etc. It depends upon your usage. Note- choose and activate only 1 plan.
3. That’s it! Now switch to UMTS in phone settings and you will get your 3G signals again with 2G plan. To check your usage, type *111*1# with your mobile keypad.
4. Hence connect your mobile to pc along with 3G signals and you will get 3G high speed downloading + surfing again and the good thing is that the usage will deduct from 2G data in MBs or KBs etc.
Enjoy! Please pass your comments below na…Anyways, Happy Holi to all my Indian Friends.
Bypass Cyberoam Security–TOR Browser
Labels - Download Softwares , How to , IP Address , Others , Security Tips , Website Hacks

Steps to Crack Cyberoam Security and access blocked sites very easily:
1. First of all download and install TOR Browser from its official site here. It is also available for MAC and other users.
2. Now after extracting all files inside, open its main TOR exe file properly.
3. Click on the following button and run the browser.
4. Please be patient because TOR Browser takes 2 mins to open with its full features.
5. Now it opens with Mozilla Firefox skin and you can access restricted sites very easily.
6. That’s it! Enjoy…
Also Note: You can also use some other anonymous proxy sites such as Kproxy, Hidemyass.com and many more instead of installing TOR Browser in your PC.
04 March 2012
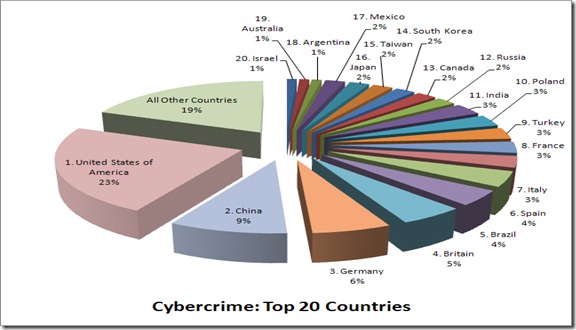
Top 20 Countries that host Cyber Crime mostly 2011
I think all of you are aware of Cyber Crime but you don't know the top countries who mostly do it. Now a days it is increasing very fast and according to a world survey, it was found that most of the crime was done in US mainly. Therefore, we have to be alert every time at every moment. Lets have an look what Patrik Runald has to say about it- “More malicious content is being hosted in Canada than ever before,” said Patrik Runald, senior manager of Security Research, Websense. “Cyber criminals are taking advantage of Canada’s clean cyber reputation, and moving shop. We’re seeing all time highs for both hosted phishing sites and bot networks. It is important for Canadian citizens to be extra vigilant on the Internet, taking extra precautions when clicking on links.” Below is a simple pie chart of top 20 Countries where cyber crime is hosted very much:
Prediction by KrackoWorld: In the coming time, Canada will be the prime target of hackers Guaranteed!
Note to Indians- Thank god! that our country India has not comes under top 10…Hurrey
Thats it!
\