Is Facebook Timeline gets Hacked in near by Future! Know why?
As you know my dear friends gaining popularity also comes with its hacks. Thus, Black hat hackers are now concentrating on Facebook Timeline hacks and cracks. Some days past Anonymous hackers gives an warning to the Facebook CEO about the Timeline vulnerability. In my point of view, this war will never ends as with the increase/development in Cyber security…Hackers should also be increased with new exploits and hacking ideas in coming future. Therefore all you have to be aware of it and sets your mind to tackle it wisely. Anyways KrackoWorld is there to help you out in any of your problem and keep smiling!!!
Some Hacking facts n figures about Facebook Timeline are:
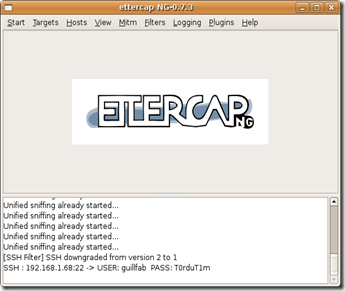
1. Now its much more easy for the hackers to hack Facebook and any other social networking accounts because they usually first gain some useful information about the user which he wants to hack and that information will be easily available at Timeline from the beginning. As in Laymen's language, Facebook Timeline will also be known as Footprinting.
2. With the development of Facebook Timeline, Google plus project of overtaking Facebook sooner will also be crushed.
3. Onwards 6 December 2011 (Facebook Timeline official launching date), more than 1 million people switched to it earlier in just 2 months approximate.
Know what Mark Zuckerberg has to say about Facebook Timeline:
I founded Facebook on the idea that people want to share and connect with people in their lives, but to do this everyone needs complete control over who they share with at all times.
This idea has been the core of Facebook since day one. When I built the first version of Facebook, almost nobody I knew wanted a public page on the internet. That seemed scary. But as long as they could make their page private, they felt safe sharing with their friends online. Control was key. With Facebook, for the first time, people had the tools they needed to do this. That's how Facebook became the world's biggest community online. We made it easy for people to feel comfortable sharing things about their real lives.
We've added many new tools since then: sharing photos, creating groups, commenting on and liking your friends' posts and recently even listening to music or watching videos together. With each new tool, we've added new privacy controls to ensure that you continue to have complete control over who sees everything you share. Because of these tools and controls, most people share many more things today than they did a few years ago.
Overall, I think we have a good history of providing transparency and control over who can see your information.
That said, I'm the first to admit that we've made a bunch of mistakes. In particular, I think that a small number of high profile mistakes, like Beacon four years ago and poor execution as we transitioned our privacy model two years ago, have often overshadowed much of the good work we've done.
Just have an look at Facebook Timeline:
That’s all for today! New Facebook Timeline Hacks will be on its way sooner..
See also- Hack Facebook accounts for free- All possible ways




 Now a days WordPress hacking is becoming common and common over 2011-12. I have also mentioned some
Now a days WordPress hacking is becoming common and common over 2011-12. I have also mentioned some 


 Now a days finding online coupons/vouchers and deals for heavy discounts at shopping websites like Amazon, eBay, Go Daddy and many more is very much difficult. Hence coupon codes makes our purchase simpler and cheaper than any other. for ex-
Now a days finding online coupons/vouchers and deals for heavy discounts at shopping websites like Amazon, eBay, Go Daddy and many more is very much difficult. Hence coupon codes makes our purchase simpler and cheaper than any other. for ex- 






![demo 1_thumb[1] demo 1_thumb[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhLXvKbKio-id09t2KMn0RsvgxF4e6jBoYZo6E70smezzlE_oPamHJb2Fe-EZ1KcxguiFfzfMfy2C8KFrpfB3ETsZbuloeZMfZ5YJPpOz7ys7s2mfkva0VZpIqosoR_xt_nu1yQksObUtVq//?imgmax=800)
![demo 2_thumb[2] demo 2_thumb[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiD5TwA0C2uMVkRyTAee6MqCSias7jb3A1WajDf47bYodKLMeTa8vpHSYl6hLGMH-peLzSuGBoXNQhPm4kB9EO40d_qTcClnKq_GyahXuQ-69BIiDyuBVNMq1X-jh_blkBWM0QGq3wxLfTU//?imgmax=800)
![demo 3_thumb[2] demo 3_thumb[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh1fxK6E9PMH7ZdHhDlLGHw_f8L-aPsEfLzSmC9d3mpS33B2PKAd_omFKpTSCp3nE3ZK3GdA9Z-UchuNTCXwmekIxrYpsbejk0bys6EMAgVvLklGTh5uLDSed9YKlNUa0Ia4JhAqUotmqGF//?imgmax=800)
![demo 4_thumb[1] demo 4_thumb[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhmuX9rK1oRz18Gtt8JB_-L6GCEwzDPedwi_-Nm_l6dD_oc0IrqSdJmugHR8iRvLX0A_38HoKlHcaF1uBJJzWiqh-_fKID6wloVoXHOi4iOhKaTjnA-1fSRekhRYwcTxTfY1CZgOT5Idbi9//?imgmax=800)