How to do Dictionary Attacks to Crack Passwords via Brutus
|
|

A dictionary attack is when a text file full of commonly used passwords, or a list of every word from the dictionary is used against a password database. Strong passwords usually aren’t vulnerable to this kind of attack. In the following example, I will use Brutus, a very common password cracker, to show a dictionary attack against an ftp server. Brutus is a Windows only program, but at the end of this chapter I will list a couple more password crackers, some of which are made for Mac, Windows, and Linux.
Dictionary Attacks
Before I get into the example, you must first know what an FTP server is. FTP stands for File Transfer Protocol. FTP is a simple way to exchange files over the internet. If a hacker got FTP access to my website, he could delete/upload anything he wants on my server. An FTP address looks similar to a website address except it uses the prefix ftp:// instead of http://. I set up an FTP server on my computer so I could demonstrate. You can get Brutus at http://www.hoobie.net/brutus/ .
Procedure :
1. First the hacker would choose a target. In this case it’s my home computer and the IP address for your home computer is 127.0.0.1 .
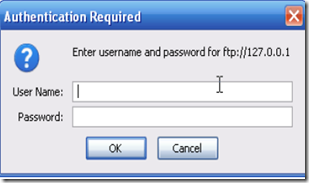
2. By going to ftp://127.0.0.1 I get a pop-up box asking for a username and password.
3. Next the hacker would launch a program similar to Brutus and attempt to crack the password.
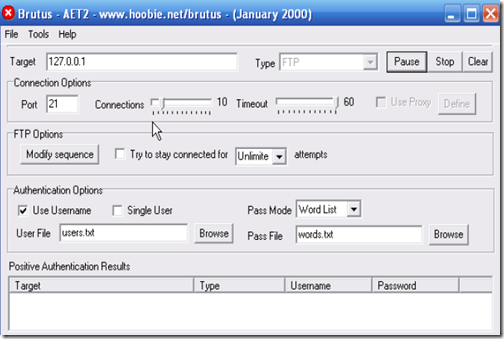
4. In the target you put the IP address of the website and to the right select the appropriate option, which in this case is FTP.
5. The default port is 21 but some websites change this to make them a little more secure. If you find out that the port isn’t 21, you can find the right one by doing a port scan.
6. If you don’t know any of the usernames for the FTP server, then you will have to get a list of the most common usernames.
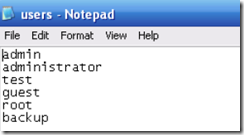
7. For a dictionary attack you will have to choose the pass mode Word List and browse and select the file containing your word list. You can get some good password lists at
http://packetstormsecurity.org/Crackers/wordlists/ . Below are examples of what a username and password list might look like.

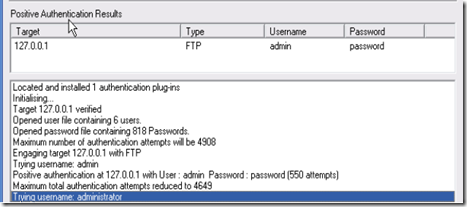
8. Once you hit Start the program will attempt to connect to the server and begin to try all the possible combinations from your lists.
9. If you’re lucky, eventually it’ll get the right Username:Password combination. As you can see below, it got the correct combination of username – admin and password – password.
10. A smarter hacker would use a proxy when using a program like this. What a proxy does is cloaks your IP address by sending your connection request through another computer before going to the target. Brutus leaves a huge log of your presence on the target server.
That’s it !
Join me on Google+
|
|
Respected Readers :-
|

E njoyed this post very much – So why not you Subscribe to our regular Email Updates ! and stay connected with us forever .


















Hack Ethics is an experienced online Private Investigator/Ethical Hacker providing investigative solutions and related services to individuals. You may find my services of use, my areas of expertise include the following: fidelity check, mobile hack and access, social media hack, email, educational institutions, clearing criminal records, accounts recovery, websites, database etc. Have you been scammed because all you were looking for was love? We can help you in 2 ways.
ReplyDelete1. Verify the person's identity before meeting the person and moving to the next step.
2. If you have been scammed online and would like to track the person's location so you can proceed with some type of action. Stop being scammed by fake hackers. Hire a Ethical Hacking game roup who are professional and real. You might be curious that what hacking group services can provide? .. If you want to hire a hacker, you should contact me at hackethics008@gmail.com or text only - +1 (630) 755-8868
Hack Ethics is an experienced online Private Investigator/Ethical Hacking Organization which have a spare master key that no one has. Providing trustworthy investigative solutions and related services to individuals within 24 hours. Contact us at - hackethics008@gmail.com or text only - +1(630) 755 8868. we can hack anything. We are totally secured and your security comes first.
ReplyDeletewe are best in our jobs which are
. Change School Grade
. Bank jobs, Flipping cash
. Hack and control any robot
. Database hack
. Remove Criminal Records
1-facebook hack
2-gmail hack
3-whatsapp hack
4-website hack
5-tracking calls
6-online hacking lectures
7-phone clone
8-online records changes
9-retrival of hacked social media accounts
10- university grades
11- android and iphone hack
12- twitter hack
13- any website hack
If you are looking for a professional Hacker that specialized in genuine hacking services. Contact our email - hackethics008@gmail.com or text only - +1(630) 755 8868
ReplyDeleteIn the world of hacking we are the best when it comes to client satisfaction. Stop being scammed by fake hackers. Hack Ethics is an experienced online Private Investigator/Ethical Hacker providing investigative solutions and related services to individuals. You might be curious that what hacking group services can provide? .. If you hire a hacker, you always have worried of losing your money. We won't keep a cent if can't do your job. 100% refund if job is not completed. Contact - hackethics008@gmail.com or text only - +1 (630) 755-8868 . We render
+University Grades Hack,
+Bank Account Hacks,
+Control devices remotely hack,
+Facebook Hacking Tricks,
+Gmail, AOL, Yahoomail, inbox, mobile phone (call and text message Hacking are available)
+Database Hacking,
+PC Computer Tricks
+Bank transfer, Western Union, Money Gram, Credit Card transfer
+Wiping of Credit,
+VPN Software,
+ATM Hack
email us now : hackethics008@gmail.com or text only - +1 (630) 755-8868
Very informative article, which you have shared here about the hacking. After reading your article I got very much information and it is very useful for us. I am thankful to you for sharing this article here. Certified Ethical Hacker for Hire online in USA
ReplyDeleteThank you for taking the time to post this blog. I am pleased with your work after reading this post. This is very useful for us. Keep sharing such blogs. hire a website hacker online
ReplyDeleteI generally check this kind of article and I found your article which is related to my interest. Genuinely it is good and instructive information. Thankful to you for sharing an article like this. Website Hacker
ReplyDeleteI'm sure you had great knowledge about this. You gave us much information. This information is really good and commentable about Hire A Cell Phone Hacker. Thanks for sharing your things with us.
ReplyDeleteI am attracted by the presentation of this article. It is a genuinely a gainful article for us. Keep posting, Thank you.Hire A Professional Website Hacker
ReplyDeleteThe representation of this article is actually superb. I think this is a genuinely beneficial and instructive article for everyone, I appreciate this kind of writing, Thankful to you for sharing an article like this.Ethical Hacker For Hire in Usa
ReplyDeleteThis is for anyone seeking to recover their data or funds lost to scammers on the internet. I sent out $132,000.00 worth of BTC to this broker named E29 Crypto Marketers. My experience was a good business proposal turned sour. l was added to a crypto learning and trading group on Telegram. I thought it was real, unfortunately, they are like other fraudsters found on the internet and online romance apps, I only knew about their fraudulent activities after losing my investment to E-29 marketers. l would have lost all my invested funds to this online scam scheme. with the quick help of these professionals in reclaiming stolen money. I found their reviews on Google, After my research about them, I concluded they were the perfect recovery expert to hire to recover my stolen cryptos. I never regret coming in contact with CYBER GENIE HACK PRO team. Within the short period I spent conversing with them during the recovery process, I learned a lot more than the four walls of a school. They can be reached via their details below: Watsapp; +1 (252) 512-0391 Telegram; CYBERGENIEHACKPRO... Web; cybergeniehackpro (.) xyz/
ReplyDeleteFRESH DATABASE FROM US UK CANADA AVAILABLE IN BULK
ReplyDeleteSPAIN GERMANY ASIAN DATABASE ALSO AVAILABLE
SCAN DL PHOTOS OF DIFFERENT COUNTRIES AVAILABLE (REAL)
FULL INFO DATABASE IN BULK QUANTITY
EMIGRANT VISA FROM DIFFERENT COUNTRIES.....
DM ME AT✆
TELE|GRAM-/@James307/
#LEADS
#DATABASE
❅JUST GET SAMPLE FIRST TO TEST QUALITY & FOR TRUST
❅GET DISCOUNT ON BULK ORDER.
❅PAYMENT METHOD IS ONLY BTC
❅GET REPLACMENT ON ANY BAD INFO
❅FILE WILL BE DELIVERED AFTER PAYMENT
❅GET SPECIFIC INFO LIKE STATES,CITIES,DOB
❅GET ANY STATE YOU WANT
SSNDOB ALL STATES + FULL INFO
SSN dOB DL NUMNER ALL STATES + FULL INFO
SCAN DL PHOTOS ALL STATES WITH RANDOM GENDER
EIN BUSINESS LEADS ALL STATES
CC WITH CVV & MMN RANDOM STATES
DOBs(2000-2015)&(1930-1950) RANDOM STATES
SSN DOB DL NUM & DL ISS+EXP RANDOM STATES
SSN DOB DL NUMBER WITH ROUNTING ACCOUNT NUMBER
SSN DOB DL NUMBER WITH EMPLOYMENT DETAILS
PROS FROM SBA|UBER|DOORDASH|AT&T|SPARK| AVAILABLE
‒‒‒‒‒‒‒
UK NIN NUMBER WITH FULL INFOs RANDOM CITIES
UK SCAN DL FOTOS
UK PASS|PORTS
UK SIN NUMBER WITH DL NUMBER
UK FRESH LEADS
UK EMAIL LEADS
‒‒‒‒‒‒‒‒
CANADA SIN NUMBER PROS
SIN NUM WITH FULL INFO
CANADA DL FOTOS
PASS|PORTS
CONTACT FOR FURTHER INQUIRES & DETAILS