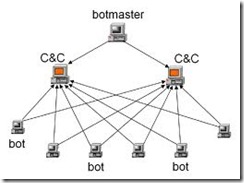
How to Make Money with Google Chromium Bounty Programs

The Purpose of The Program
This Vulnerability Rewards Program was created to help reward the contributions of security researchers who invest their time & effort in helping us to make Chromium more secure. Through this program we provide monetary awards and public recognition for vulnerabilities responsibly disclosed to the Chromium project and many more.
Some FAQ’s
What reward might I get?
Our base reward for eligible bugs is $500, but the typical payout is usually at least $1000. If the rewards panel finds the bug particularly severe, the value can be as much as $3133.70. Or if the rewards panel finds a report really impressive, the value can be as much as $10,000 or even beyond. To ensure the greatest chance at the maximum possible award please adhere to the guidelines provided in the Reporting Security Bugs.
What bugs are eligible?
Any security bug may be considered. We will typically focus on High and Critical impact bugs, but any clever vulnerability at any severity might get a reward. Obviously, your bug won't be eligible if you worked on the code or review in the area in question.
Who pays for the awards program?
As a consumer of the Chromium open source project, Google sponsors the rewards.
How do I find if out my bug was eligible?
You will see a provisional comment to that effect in the bug entry once we have triaged the bug etc.
What if someone else also found the same bug?
Only the first report of a given issue that we were previously unaware of is eligible. In the event of a duplicate submission, the earliest filed bug report in the bug tracker is considered the first report.
For more information, please Visit Here.
Also Read- How Hackers can Make Money with PayPal Bug Bounty Programs?